By Roger V. Skalbeck (aka @weblawlib) and Meg Kribble (aka @mak506)
During the 2009 American Association of Law Libraries (“AALL”) annual meeting, there were several social media options for sharing experiences, opinions and content about the conference. Using the keyword AALL2009, people could tag photos on Flickr and categorize shared bookmarks on Delicious.com. However, without a doubt, the majority of social media activity during the conference took place on Twitter. Between Friday, July 24 and Wednesday, July 29, 146 different Twitter accounts were used to post 1,264 conference-related messages. These were identified with the hashtag #aall2009. A hashtag is a pound sign (#) followed by any string of characters. The Twitter site generates an automatic search for any characters following a # sign, and most Twitter clients treat this as a group tag.
Since reaching its tipping point at South by Southwest Interactive in 2007, Twitter has become the unofficial backchannel of many conferences. Librarians, techies and political activists–just to name a few categories–now commonly use Twitter at conferences, and it is steadily moving forward. Savvy moderators have begun to request that questions and comments from Twitter be relayed to the room, which happened at a Library 2.0 symposium hosted by the Yale Information Society Project in April. At this year’s CALI conference, Tom Boone and Jason Eiseman experimented with projecting the conference hashtag Twitter feed during their presentation.
To better understand the hashtag concept, read the article How to: Get the Most out of Twitter Hashtags. This article notes that conferences and events “rely on the hashtag system more than almost any other entity.” This year’s AALL conference was no exception. Now that the conference is over, this is a great chance to look at conference-related Twitter activity, searching for possible meaning or moral lessons. If you attended the conference but didn’t follow Twitter, here’s an insight into what you may have missed, and what you might look forward to trying at the next conference you attend.
Tweet Topics
To visualize what people were posting to Twitter during the AALL meeting, librarian Jason Eiseman created a word cloud of all posts marked with the #aall2009 hashtag. The more frequently a word was used, the larger it appears in the graphic. It is perhaps unsurprising that “law” and “library” appear as the biggest topics.
On Twitter, updates occur in real time, allowing instant back-and-forth sharing of ideas about presentations and reactions to the content discussed. For many, Twitter functioned almost as a chat room during the conference. Following the hashtag created windows into other sessions going on at the same time as the one you were attending. In addition, people unable to attend the annual meeting joined in the conference conversation by following the hashtag and sending reactions to posts and questions to attendees. Twitter also made it easy to find impromptu lunch dates–and ideas for where to have lunch. More on that later.
Community Standards and Anonymous Posting
During the conference keynote, Professor Jonathan Zittrain spoke about community standards online. He illustrated a positive form of these standards through a situation with a Wikipedia entry about “The Star Wars Kid“, a YouTube phenomenon from a few years ago. The video was posted without the kid’s permission, and he was embarrassed by the attention he received, including mention of his name in a USA Today article. On the discussion page of the article describing “The Star Wars Kid,” the Wikipedia community decided to respect his desire to have his name excluded from the entry. As Zittrain noted in The Times, “Online masses 1, USA Today 0.”
Anybody following the AALL conference on Twitter could witness a similar form of community standards develop, involving questions of taste and personal privacy. For the conference, Brian L. Baker created a new, shared Twitter account @aallsecrets, where people could post anonymous updates, providing an outlet for inner secrets, negative reactions to the conference, or other anonymous humorous and random thoughts. The account password was publicized shortly before the conference, so anyone could post new messages, delete messages, remove personally identifiable information and re-post items others had deleted. There was even a bit of back-and-forth between one person deleting a message and another posting a tip on how to recover deleted messages. The post with the “recover deleted messages” directions was added and removed at least three times.
Baker was inspired to create @aallsecrets because of a similar account created for the American Library Association (ALA) 2009 conference in Chicago the previous month. In Chicago, the @alasecrets account was used to post anonymous information that was often racy, snarky and bordering on offensive to some. At one point, someone who disapproved of @alasecrets shut it down by making the posts private and changing the password, leading to the creation of @alasecrets2009, which was set up so that posts had to be emailed instead of using a shared password.
With more than 27,000 people attending the ALA conference, there was a greater chance that something controversial would be posted. However, there is a distinct possibility that like some of the more outrageous posts on @alasecrets, as well as those on @aallsecrets, were also fictitious. For example, one of the authors of this article witnessed a few law librarians cluelessly asking each other about symptoms of cocaine use, with the clear intent of spicing up the @aallsecrets content!
The identity of authors of specific @aallsecrets posts became open secrets among some attendees. In smaller groups, some people admitted to posting (or deleting!) certain items, either freely or on being asked about them. One @aallsecrets poster, wanting to send a message to a vendor but perhaps without wanting to be contacted by the vendor to discuss the matter, posted “Thanks for the salad, West. Way to be different. Love, the vegetarians.” The borrowed smart phone on which this message was posted was then passed around approvingly among about half a dozen conference goers.
The @aallsecrets account also served as a venue for those with unpopular opinions. During session G-2 Unmasking a Marvel of an Idea in D.C.: How Graphic Literature Can Be Supertools for Law Librarians, someone who was more skeptical of the concept of using pop culture stories to inform legal research teaching used @aallsecrets to express his or her true feelings on the subject. There was some lively back and forth with people who found the session illuminating posting under their personal Twitter accounts.
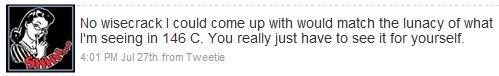
In addition, a number of @aallsecrets were critical of presentation styles in general, zinging presenters for reading their slides and using templates that consisted of black text on a white background.
The authors of this article posted to @aallsecrets and deleted posts, and one of us had at least one post deleted. Further, Meg admits that at one point during the conference, she nearly posted a brief version of her thoughts on a matter on @aallsecrets, but decided the issue was something that she should own, so the tweet was jettisoned in favor of a blog post after the conference.
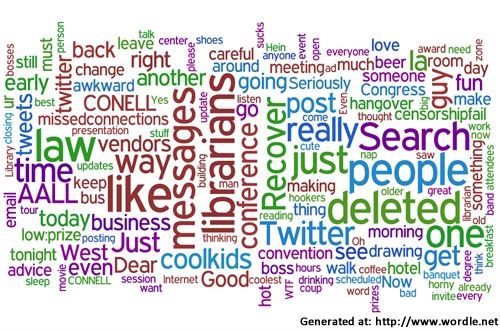
To get a flavor of the secrets law librarians shared this year in Washington, D.C., take a look at the word cloud of the Twitter updates posted to the @aallsecrets account, which includes deleted and re-posted updates.
Here are a few selected posts from the account.
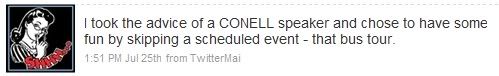
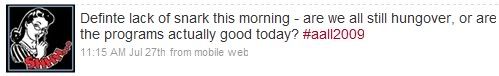
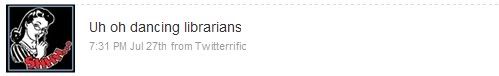
During the conference, though many messages were deleted and at times re-posted, no one shut down the account. Any user could have changed the password and cut off access, as happened with the original @alasecrets account. Nobody went that far. This is a good sign that the community of people who used the account not only cared enough to tend it, but remained committed to the free exchange of information regardless of how critical, potentially controversial, or silly it was. There are clearly differing opinions about good taste and appropriate behavior, but no single person ruined it for the crowd.
Secrets and Privacy
By the end of the day on Wednesday, July 29, the @aallsecrets account was no longer accessible, as someone anonymously changed the shared password. The final post? “With #aall2009 in the books, @aallsecrets is closed for business until #aall2010 in Denver. Thanks to everyone!” It was after this post that Baker revealed himself as the creator of @aallsecrets by tweeting to request that the person who closed it get in touch with him. Baker acknowledged that he was the creator of the account and had intended to leave it open year round. He has subsequently informed us that the account is “in good hands.”
We were later able to chat with the holder of the password, who revealed that the reason for closing @aallsecrets until next year was a privacy hole in one of the methods people used to post to it. Twittermail, which enables users to email updates to a Twitter account, saves the email address of the last person to post to it for anyone else using the service to see. This placed “Good Hands” in a quandary. As Good Hands told us, “posting [details of the privacy hole] to secrets would’ve sent everyone to the settings page to see that I had posted it. Posting to my own account would’ve sent everyone there to see the identity of whoever had posted last.” Even if Good Hands had posted to the @aallsecrets account by another means, people would still be able to see the identity of the last person to post via Twittermail. The creators of Twittermail clearly did not foresee its use for this type of shared account, but for a venue that is intended to allow people to post anonymously, privacy is a big deal. Good Hands speculated that perhaps next year an anonymous remailer or a third-party email account run by an uninvolved party could be set up, but even if people were told an address is anonymous, “what reason do they have to trust us?”
Competition for Snarky Posts
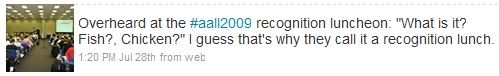
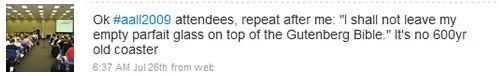
@aallsecrets was not the only anonymous Twitter account providing snarky updates. As the conference was about to begin, several Twitter users noticed updates from the ironically named account @LastTimeAtendee. Countering the multi-author approach of @aallsecrets, @LastTimeAtendee seemed to be a single person trying to portray a sort of humorous zeitgeist of the conference. Updates ranged from the asinine to the absurd. Here are two typical tweets:
Hashtag Humor
Because hashtags for conferences and other events have become so ubiquitous, many Twitter users create their own for humorous effect. Here are some of the “for fun” hashtags from the #aall2009 tweets and @aallsecrets account:
#aall2009missedconnections, #aallrecoveryplan, #censorshipfail, #cheap, #coolkids, #dontbethesnorer, #everyoneelseisageektoo, #gonorthgeorgia, #justkidding, #notreally, #ohyessheisaninja, #seriouslythisisthecoolestprogramever, #thingsthatwouldhavebeengoodtoknowSunday, #totebag
In addition to the humorous hashtags, some other hashtags were employed to specify conference-related events. They included:
#ci, #genxy, #heinfunrun, #karaokeken09, #lawberry, #w2c2009
Conversation Hijacking and Crowd Competition
Any unmoderated online resource runs the risk of getting bombarded by spam or dominated by just a few individuals. As it turns out, the conversation during AALL2009 was evenly distributed, and discourse was mostly civil and self-regulated, even in the anonymous postings. On Twitter, talk is cheap. Talk is also short. This creates a potential for making a cheap joke, just to get noticed. However, with the whole world potentially watching, the risk of eroding a good reputation or losing peer respect can be a reasonable regulator of good taste.
Twitter hashtags are completely open for anybody to use, so there is no separation between personal, promotional and professional posts. Buyers and sellers, friends and foes can all join the conversation. During AALL2009, a few vendors picked up on the conference hashtag, posting conference updates and related news. These vendors offered product updates, mentioned conference offerings and even invited librarians to receptions.
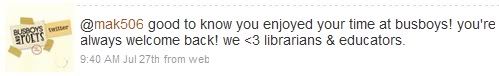
Even local businesses found the conference chatter and joined the conversation. The Gen X / Gen Y Caucus held its social event at the Busboys & Poets bar and restaurant. Something about the establishment’s ambience made some attendees suspect they might be on Twitter, and sure enough, they are. Although Caucus leadership mailed a print thank you letter after returning home, a few Caucus members instantly thanked them through Twitter. Busboys noticed our tweets, and replied to us a couple times, even using the #aall2009 hashtag.
Rosa Mexicano, another restaurant enjoyed by law librarians while in DC, was a bit slower, finding our tweets and following us only after we had returned home. Nevertheless, Twitter proved useful here when some of us were enticed to visit Rosa Mexicano by pictures of freshly made guacamole posted to Twitter by other librarians!
Conclusion & Suggestions
In closing, we offer some thoughts on hashtags, conference coordination and community standards, each limited to 140 characters or less. If you like any, feel free to tweet them.
- #hashtags are valuable conference planning tools. Publicize them in advance.
- #aall2010 is already being used as a tag for next year’s AALL conference.
- Twitter is highly useful as a conference backchannel–and becoming increasingly useful when used officially at conferences
- if you can’t attend a conference, following the Twitter hashtag is the next best thing to being there
- reputation and respect are good regulators of decent Twitter behavior
- a conference with 27,000 librarians stirs more secret twitter controversy, real or fictional, than one with 2,000
- Tweetchat makes it easy to follow conference conversation if you have a Twitter account
- If you’re not on Twitter, you can still follow hashtags live with sites like Twitterfall, Tweetgrid or the Sideline software
- Unique hashtags work best. The CALI conference chose #calicon09 not #cali09, to avoid confusion with California.
Let us know what you think, tweeting publicly or by direct message to @weblawlib and @mak506!
Related Stories and Additional Reading
How to: Get the Most out of Twitter Hashtags
By Ben Parr, May 17th, 2009, Mashable: The Social Media Guide
A simple way to avoid being the next Star Wars Kid
By Jonathan Zittrain, Times Online, May 4, 2008
ALA Conference 2009: Twitter Confidential – @ALAsecrets Interview
ALA 2009: This week, LJ caught up with the mastermind behind the @ALAsecrets Twitter account that aired some of the recent conference’s dirty laundry and raised a few eyebrows
Josh Hadro — Library Journal, 7/21/2009
Library Conference Secret Twitter Proves Librarians Sexy, Stern
Posted by Amanda Hess on Jul. 13, 2009, at 9:59 am
Sexy Secrets From Librarians: The Lost Tweets
Posted by Amanda Hess on Jul. 14, 2009, at 9:42 am
Goodbye, Sexy Librarians (See You Next Halloween)
Posted by Amanda Hess on Jul. 15, 2009, at 10:30 am
Case Study: Twitter Usage at WordCamp SF
Wednesday, June 24, 20009